Since the start of 2024, there have been 5,300 school districts that suffered a data breach. These schools are all in the United States. In 2021, 56% of schools reported data breaches. In 2022, 80% of schools reported ransomware attacks (source). Almost half resulted in ransom payments (source). Massive data leaks expose sensitive information. This information ends up on the dark web in the hands of nefarious individuals. It is a big money business. Let’s explore a free resource by K12 SIX that’s available to K-12 schools in the United States.
Assessing the Extent of the Problem
Lack of reporting requirements makes it difficult to determine the extent of data breaches. That aside, data leaks affect thousands of teachers, staff, parents, and guardians. In 2023, monetary losses to school districts from cyberattacks ranged from $50K to $1M. This monetary loss is per incident. In 2021, 771 institutions were affected, which is about 2.6 million records (source).
With so much going wrong, what actions can you take? Try this one on for size.
K12 SIX operates as an information sharing and analysis center (ISAC) exclusively for the K-12 education sector. The K12 Security Information eXchange (K12 SIX) is a national nonprofit organization dedicated to protecting the U.S. K-12 community—including school districts, charter schools, private schools, and regional and state education agencies—from emerging cybersecurity threats.
Learn More About K12 SIX
Explore the K12 SIX Essential Series
The K12 SIX Essentials series offers tools and advice for U.S. schools. The goal is to help schools meet basic cybersecurity standards. The resource, devised by K-12 IT experts, includes:
- Guides on cybersecurity frameworks for K-12 leaders
- Essential protections and how to implement them for the 2023-2024 school year
- A self-assessment tool for districts
- A Cyber Incident Response Guide
- Info on cybersecurity grants
These resources aim to help leaders manage cybersecurity efforts. With rising cybersecurity threats, protecting schools is vital. The K12 SIX Essentials help districts protect everyone and their data. Combine them with CISA and Google advice.
How to Get the Series
Getting the series of documents (PDF) is easy. Go to their website and fill out the online form. Once you do so, you will be able to access the page with all the PDFs. The intent of these documents is to make a resource more accessible than others available. Others include the MITRE Framework.
The Incident Response Runbook
Several insightful documents are available in the K12 SIX series, but let’s take a closer look at one near and dear to my heart: the Cyber Incident Response Runbook v1.1. It is the resource any CTO will reach for after a data breach or ransomware attack.
Aligned to the NIST Computer Security Incident Response Lifecycle, developed with the input of K-12 IT practitioners, the K12 SIX Essential Cyber Incident Response Runbook is tailored specifically to the needs and context of K-12 organizations. It offers guidance for coordination with internal and external partners, stakeholder communications, and managing student-initiated incidents.
Cybersecurity Guides for Schools
Here are some of the suggested actions in the runbook summarized:
- Cyber Crisis: What Counts? Identify cyber incidents like technology misuse, phishing, and ransomware attacks.
- Heroes of the Cyber Front: Roles Defined. Detail roles within the Incident Response Team, including leadership and communications duties.
- Who You Gonna Call? Cyber Allies! Keep a list of essential contacts, encompassing IT, legal, executive leadership, and law enforcement.
- Blueprints for Battle: Plan Review. Examine existing emergency, business continuity, and disaster recovery plans.
- Ready, Set, Communicate: Prep Talk. Prepare communications with draft notifications, update protocols, and alternative communication methods if systems go down.
- First Clues: Logging the Cyber Trail. Record actions, inform leadership, and secure evidence upon detecting an incident, maintaining the integrity of the investigation.
- Containment Crew: Sealing the Breach. Isolate compromised systems, disable breached accounts, and apply security controls to limit damage.
- Virus Vanquishers: Cleaning House. Patch vulnerabilities, remove malware, reset passwords, and potentially rebuild affected systems.
- Phoenix Protocol: Rising from the Ashes. Restore systems from clean backups, implement new security measures to prevent recurrence, and monitor for signs of re-compromise.
- Reflections and Lessons from the Cyber Storm. Conduct a post-incident review to identify deficiencies, determine root causes, document lessons learned, and update executive leadership on cybersecurity program improvements.
Each of these areas is elaborated on in more detail within K12 SIX’s Cyber Incident Response Runbook v1.1. Other documents complement this guide in the K12 SIX Essentials series. Definitely check out this approachable series of guides on a topic that is no joke!








 something because of their interests. This helps me see how students are using technology when they are looking for specific information or want to learn a skill. Only 9% of both middle and high school students post a question on a discussion board or a forum. Do we need to be more intentional in using this type of application? Do they just not know how, or have they found better ways to seek answers to their questions?
something because of their interests. This helps me see how students are using technology when they are looking for specific information or want to learn a skill. Only 9% of both middle and high school students post a question on a discussion board or a forum. Do we need to be more intentional in using this type of application? Do they just not know how, or have they found better ways to seek answers to their questions?  I also discovered that 43% of my teachers are facilitating student collaboration projects using online tools. This is such a great skill. How can I leverage these teachers to help other teachers do this as well? Also, I’m pleasantly surprised that 44% of my teachers are using an online curriculum. However, I want to know more. What is the frequency? Are they occasionally doing this or is this something they use every day? I also want to know what they are using. Are they using the district’s Learning Management System, or is it an online textbook?
I also discovered that 43% of my teachers are facilitating student collaboration projects using online tools. This is such a great skill. How can I leverage these teachers to help other teachers do this as well? Also, I’m pleasantly surprised that 44% of my teachers are using an online curriculum. However, I want to know more. What is the frequency? Are they occasionally doing this or is this something they use every day? I also want to know what they are using. Are they using the district’s Learning Management System, or is it an online textbook?  integrate digital content, tools, and resources into their daily instruction. 51% said they wished they had a classroom set of digital devices. 49% said they needed to know that their students had adequate broadband access outside of school and 46% indicated they were concerned that they didn’t have consistent, reliable internet access within school. Maybe I need to have my staff do some focus groups related to internet access and speed. Looking at my network resources, they should have adequate bandwidth, but maybe something is happening on campus that I am not aware of. While my team is on campus, I probably should also have them ask teachers about the availability of technical support since 47% of the teachers indicated it was lacking. And lastly, my teachers still need time to plan with their colleagues (60%) and additional professional development (50%). I need more staff to be able to meet this need!
integrate digital content, tools, and resources into their daily instruction. 51% said they wished they had a classroom set of digital devices. 49% said they needed to know that their students had adequate broadband access outside of school and 46% indicated they were concerned that they didn’t have consistent, reliable internet access within school. Maybe I need to have my staff do some focus groups related to internet access and speed. Looking at my network resources, they should have adequate bandwidth, but maybe something is happening on campus that I am not aware of. While my team is on campus, I probably should also have them ask teachers about the availability of technical support since 47% of the teachers indicated it was lacking. And lastly, my teachers still need time to plan with their colleagues (60%) and additional professional development (50%). I need more staff to be able to meet this need! 
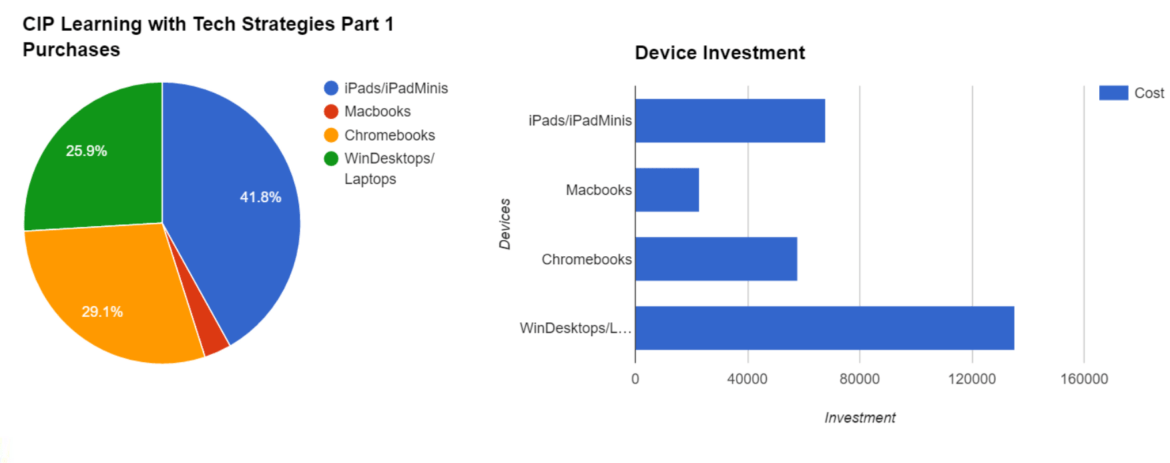
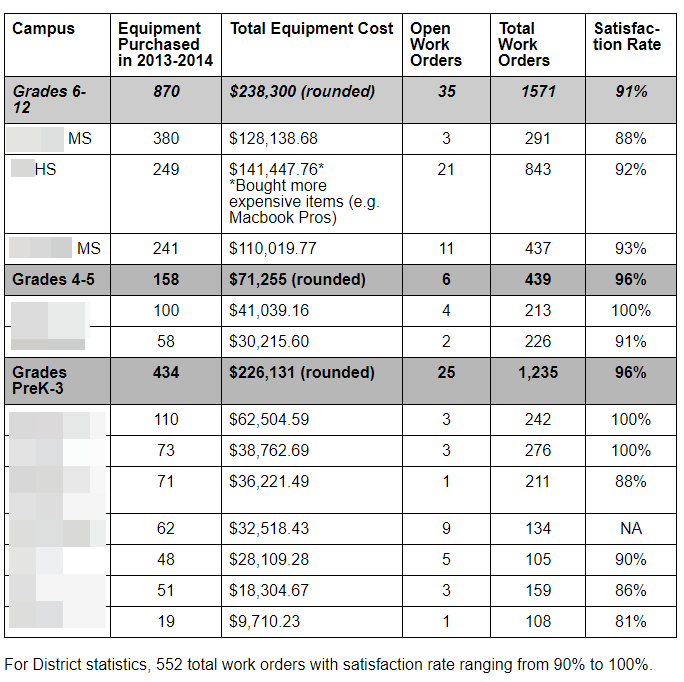
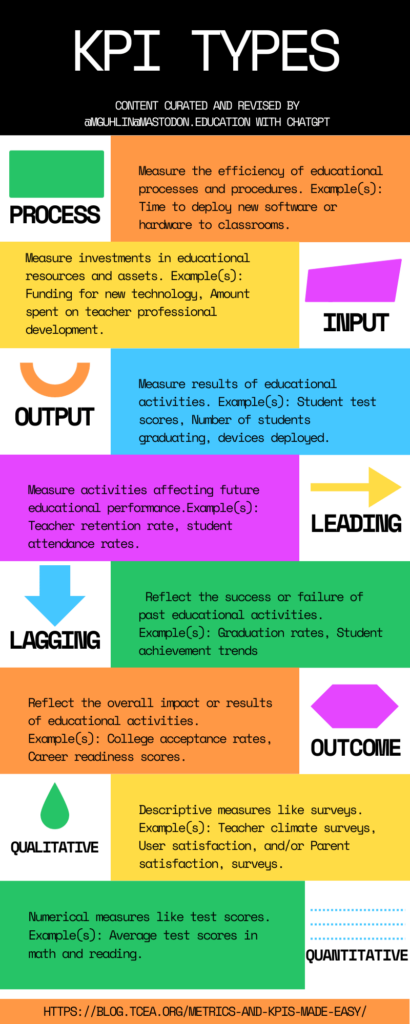
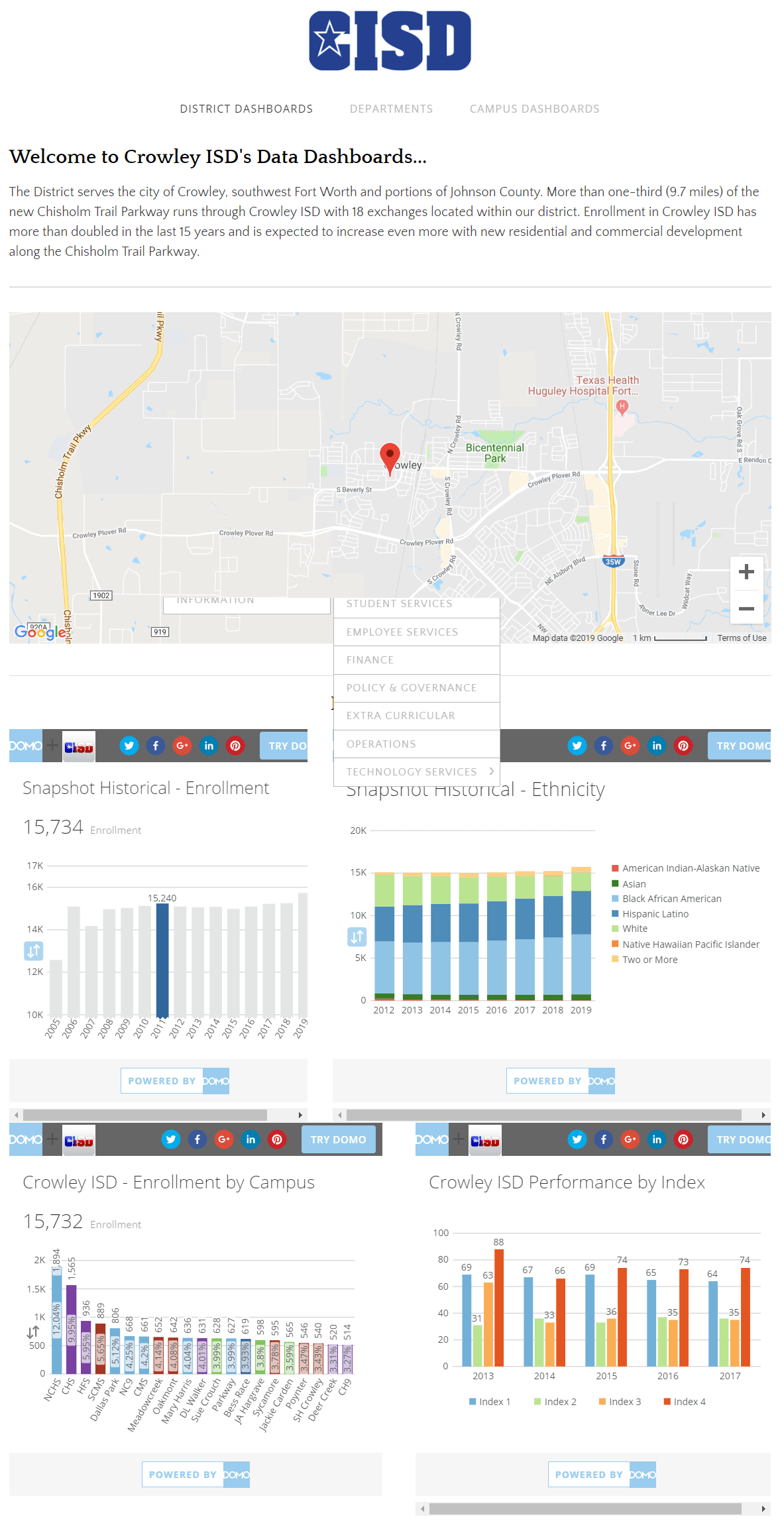
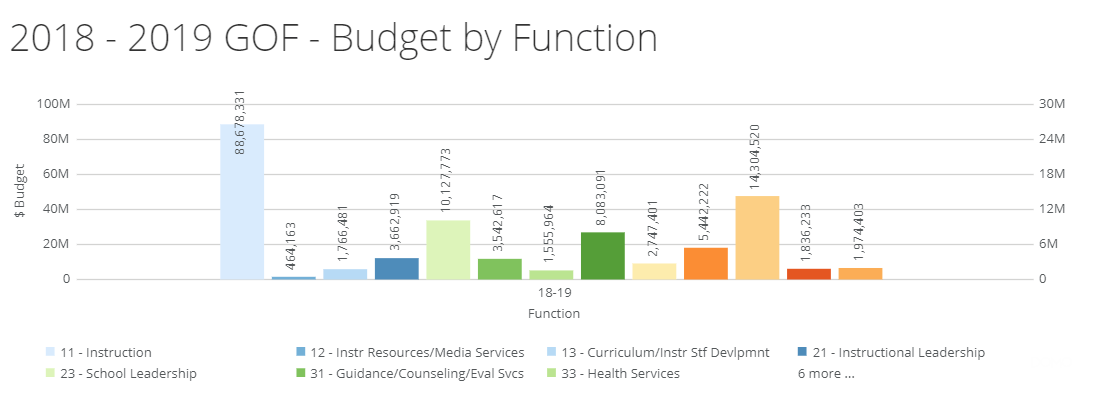
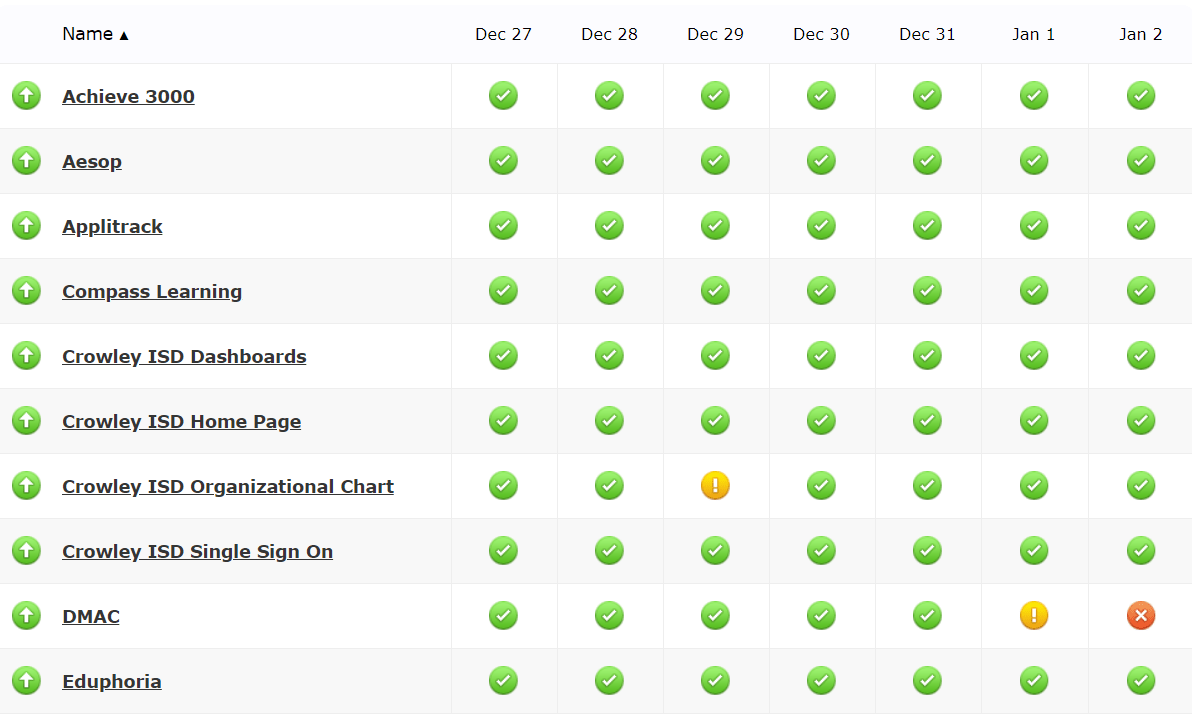
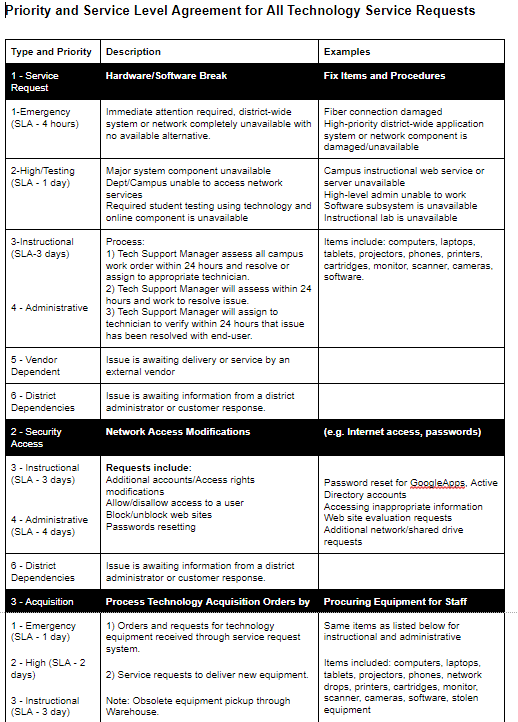

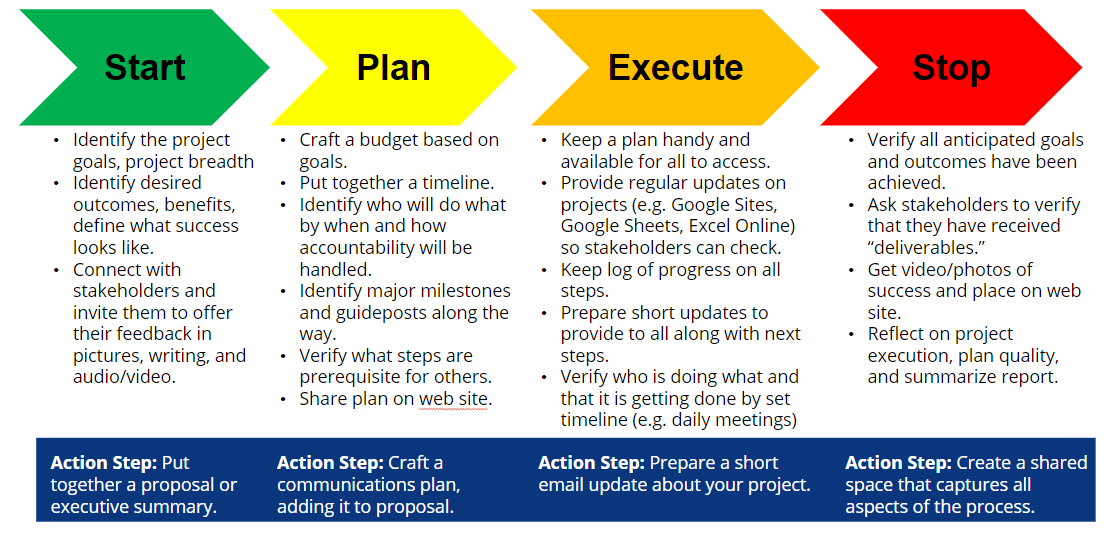
 Identify the project goals and scope, define success, and connect with stakeholders. To achieve this, I put together an executive summary. You can read about various proposal forms and executive summaries in my series. The three-part series,
Identify the project goals and scope, define success, and connect with stakeholders. To achieve this, I put together an executive summary. You can read about various proposal forms and executive summaries in my series. The three-part series,