Read the great news? The Texas Education Agency is working to provide funding for anti-malicious activities. That is, the Texas Legislature approved funding to provide cybersecurity resources to schools through the K-12 Cybersecurity Initiative. What’s available or possible? Let’s take a look at what will be available and some potential implications.
Per the CISA, NSA, and FBI, for 2022, the top 12 most exploited vulnerabilities included exploiting older software vulnerabilities and unpatched, internet-facing system (source). What does this mean for schools? Quite a bit. Many schools have a slow equipment replacement schedule to save money. This results in obsolete computers running vulnerable operating systems.
Did You Know About School Safety Planning website?
Be sure to check out U.S. government’s School Safety Planning website. It offers a variety of tools, including a Grants Finder tool, Safety Readiness Tool, Resource Search, State Search Tool, Communications and Events Center.
Why Is This Important?
Have you seen the news reporting data breaches affecting schools and organizations? Consider these from this June:
- “Employees of the San Luis Obispo County Office of Education should keep an eye on their bank accounts — a cyber attack may have leaked their financial information last week.” Read more.
- “The ransomware operation behind a cyberattack on the University of Manchester has begun to email students, warning that their data will soon be leaked after an extortion demand was not paid.” Read more.
- Uptick in Direct Deposit Scams Targeting School Districts. Read more.
A recent survey in school districts discovered the following related to cybersecurity:
“Only one-third of districts have a full-time equivalent employee (FTE) dedicated to network security. Two-thirds of EdTech Leaders feel their district has insufficient resources to deal with cybersecurity issues, which likely includes the 12% of districts that do not allocate any funds for cybersecurity defense. Yet, EdTech Leaders tend to underestimate the threats to their network: 50% or more rated five threat types as relatively low.”
Read source report.
In this gap, the Texas Education Agency is stepping in to assist in the face of cybersecurity challenges all are facing with funding and resources. One example is rampant ransomware, like the one shown below. As the tools get easier to use, ransomware bad actors are taking advantage.

TEA Offers Vulnerability Notification Service
Were you aware that TCEA actively supported this cybersecurity initiative bringing funding to Texas schools? One of the benefits of TCEA’s advocacy and TEA’s efforts is access to a free web application vulnerability notification service. That service is Dorkbot, and access begins as of July 1, 2023.
Dorkbot automates the discovery and verification of web application vulnerabilities. It does so across entire domains at scale. It hunts for SQLi, XSS, and other less common vulnerabilities. It leverages search engine cache and other public sources of indexed sites. Upon vulnerability identification, remediation instructions are sent to your security inbox. You will receive a monthly summary report of Dorkbot activities.
Since its launch over 2 years ago, Dorkbot coverage has grown. It encompasses over 2,400 institutions. This includes 99% of the largest doctoral research institutions in the US. Also, 100% of all US HBCUs and most all top institutions of higher education across 205 countries.
How to Sign Up for Dorkbot
How do you sign up for Dorkbot? You don’t. You simply have to make sure your cybersecurity coordinator’s contact email is up to date in AskTED. TEA’s announcement states the following:
Currently designated cybersecurity coordinators for each LEA will be the point of contact for any findings the service uncovers, so please ensure those designations are up to date in AskTED.
Please reach out to your district AskTED coordinator or email askted@tea.texas.gov if you need assistance with updating AskTED.
But what else will be available?
A Bird’s Eye View
Starting September 1, 2023 through August 31, 2025, Local Education Agencies are encouraged to put in place or get the following:
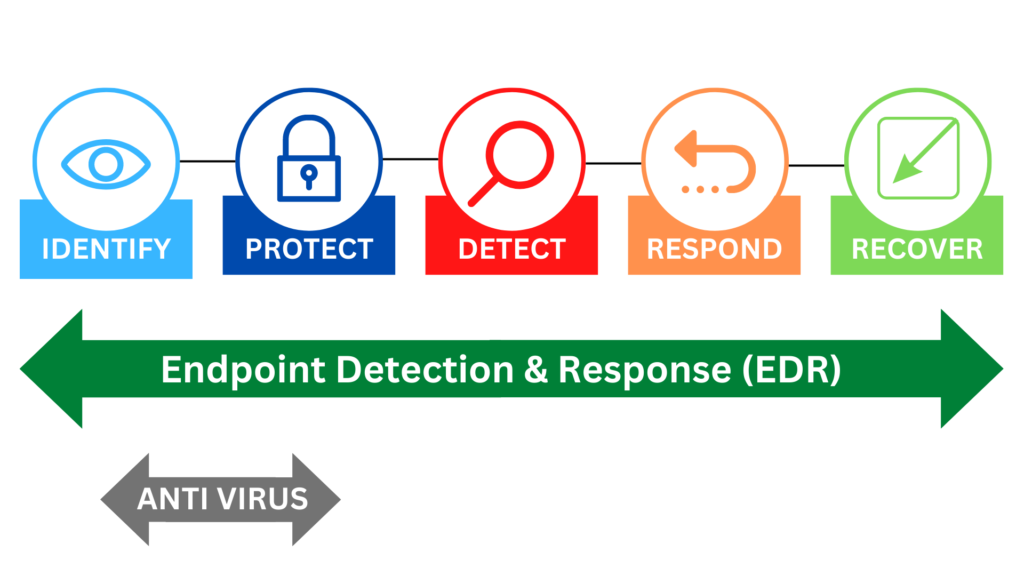
- Endpoint Detection and Response (EDR) on servers and staff devices
- Multi-Factor Authentication (MFA) on staff email systems
- Email protocol security configuration
- Restricted local admin access
- Network Detection and Response (NDR) for school surveillance and Internet of Things (IoT) devices
Let’s break each of these down piece by piece. This information is based on this announcement from TEA.
1. Endpoint Detection and Response (EDR)
Back in the day, you’d install antivirus software and forget about it. If your device got infected, antivirus software would attempt to clean it. It didn’t work so well all the time. Then spyware, ransomware, and other bad things happened, creating more and more complex cybersecurity issues. A more comprehensive solution was needed. Sometimes, the only solution was a wipe of the hard drive, with potential loss of data. That’s what made Chromebooks so useful. Since data is stored in the cloud, there’s little loss of data if a device is power-washed.
Now, EDR, or endpoint detection and threat response (EDTR), is a bit more active with cybersecurity, and TEA’s cybersecurity initiative will help with funding (“prioritized for small and midsize LEAs”). Instead of trying to fix the problem after the fact, EDR/EDTR solutions work in real-time to do the following:
- Notice bad actors
- Detect patterns of malicious activities and take action
- Engage in automated defense before an attack happens
- Provide historical and real-time viewing of issues
The main benefits? Automated response, increased analysis, and powerful monitoring notify you of what’s happening.
Schools often can’t afford endpoint detection and response. In my own experience, the more automated, the greater the cost. The Texas Education Agency (TEA) inclusion of these in the DIR will make them much more affordable.
Some school districts are using one set of tools now, but given TEA funding, are considering others. Some possible solutions include (in no particular order):
- PC Matic
- CrowdStrike
- Sophos
- Microsoft
- Carbon Black
- Cisco
- Palo Alto Networks
- Nomic Networks (f.k.a. Sentinel IPS)
These are only a few of the available solutions. Feel free to share your preference in the comments.
2. Multi-Factor Authentication for Staff Email
Relying on Google Authenticator every day can be a pain. I use it to safeguard all my Google accounts. Some districts haven’t yet implemented MFA, even though it is available for Google and Microsoft.
For password management, I rely on Bitwarden. It helps me manage over fifty account logins for work-related accounts. That’s an unbelievable amount of usernames and passwords. In my school district experience, I have found single sign-on (SSO) to be critical. It’s unreasonable to expect anyone to try and remember complex passwords.

Today, many rely on an extra level of protection. That protection is multi-factor authentication (MFA). While I rely on Google Authenticator, larger school districts rely on authentication apps. Districts integrate authentication apps into the systems they rely on.
Some define MFA as:
Authentication using two or more factors to achieve authentication. Factors include:
(i) something you know (e.g., password/personal identification number [PIN]);
(ii) something you have (e.g., cryptographic identification device, token); or
(iii) something you are (e.g., biometric).
One district in my experience relies on Microsoft Authenticator with Microsoft 365. This ensures that staff who may type anything in for a password are actually the ones logging in. And, given the data breaches that occur in school districts, that’s critical.
Did You Know?
Want to get staff up to speed on safeguarding sensitive data? TCEA’s Cybersecurity for Educators: Data Guardian online, self-paced course can help with that. What’s more, if you need customization of an online course to address your school’s policy, let us know. We can set up a custom course that addresses your needs.
3. Email Protocol Security Configuration
You are already familiar with a variety of email security protocols. Those include (source):
- Secure Socket Layer (SSL)/Transport Layer Security (TLS) for HTTPS. This secures network traffic between your device and the server. It does this through encrypted web traffic, which results in encrypted email.
- SMTPS Secure. This relies on TLS to encrypt messages between client devices and servers. This could be like between your Chromebook and Google’s servers.
- STARTTLS. This protocol allows for encryption and authentication algorithms to safeguard email traffic, including message content and metadata.
There are many other protocols, including OpenPGP/GPG. These allow end users to encrypt email messages with a digital key so that only the recipient (with a corresponding key) can open it. Often, email protocols don’t encrypt attachments to messages, so you may have to encrypt those as well.
Individuals can rely on third-party encryption tools. Implementing email encryption across a school district can be cost-prohibitive. While it is doubtful cybersecurity funding will be fully available for that, putting essential protocols in place is important.
4. Restricted Local Admin Access
Any teacher who wanted to install a new software program they picked up at a conference has run into this wall. Usually, restrictions prevent end-users from installing unapproved software. When that unapproved software is installed, it could interact negatively with the local machine, as well as the network. Worse, if ransomware, it could spread over the network to other machines and servers.
After the malware scares of 2000s, when it knocked entire campuses offline through spyware, viruses spreading unchecked through the network, it became critical to lock machines down. Users lost the ability to install software on their computers and devices. Only pre-approved software could be loaded onto a device.
While it’s tempting to allow local administrator rights to end-users, school districts should restrict that. Most computers and devices are managed remotely, with updates pushed out periodically. End users (teachers, administrators, students) simply use the devices provided.
This is what has made Google’s Chromebook such a powerful player in the education space. It is easy to manage without expensive solutions. As a technology director, I can see the benefits of not having to pay for a device management software solution or appliance.
5. Network Detection and Response (NDR)
In the past, monitoring the network was the role of a network security analyst. Now, network monitoring is increasingly automated through machine learning. Networks get a baseline assessment, then anything deviating from that baseline sends out an alarm. Analyzing raw network traffic can be almost impossible with all the devices connecting. While EDR watches devices in real-time and automates response, NDR studies the network.
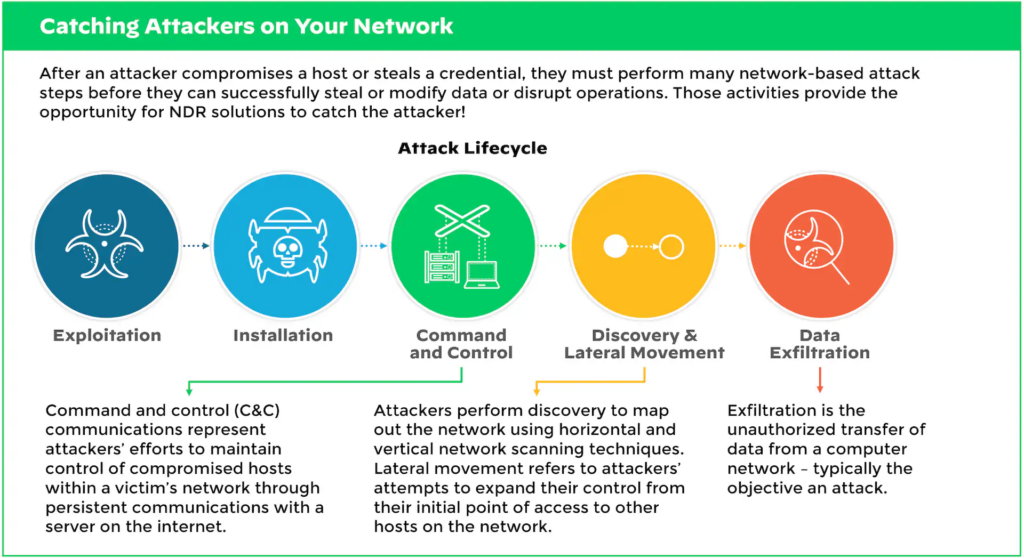
School districts pay a lot of money for NDR services, so having extra funding to cover costs is helpful.
How Much Will TEA Pay?
TEA K-12 Cybersecurity Initiative funding will fund limited distribution for Endpoint Detection and Response (EDR) on servers and devices. It would be nifty if there were some generic solutions available at a lower cost. In that way, schools could implement them in their situation. Or perhaps, they may become available at various tiers.