Safeguarding your data and devices grows more important every day. In July 2023, the Biden-Harris Administration announced a new certification program for smart devices, like your television set. This cybersecurity and labeling program is intended to assist Americans in choosing safer devices. As the Biden-Harris Administration continues to shine a spotlight on cybersecurity focused on the Internet of Things, schools must do the same with their data. That’s why the Texas Education Agency (TEA) approved cybersecurity funding for schools. But more can be done. As we end Cybersecurity Awareness Month, let’s discuss encrypting and protecting data.
The new “U.S. Cyber Trust Mark” program proposed by Federal Communications Commission (FCC) Chairwoman Jessica Rosenworcel would raise the bar for cybersecurity across common devices, including smart refrigerators, smart microwaves, smart televisions, smart climate control systems, smart fitness trackers, and more.
The White House
The Data Breach Experience
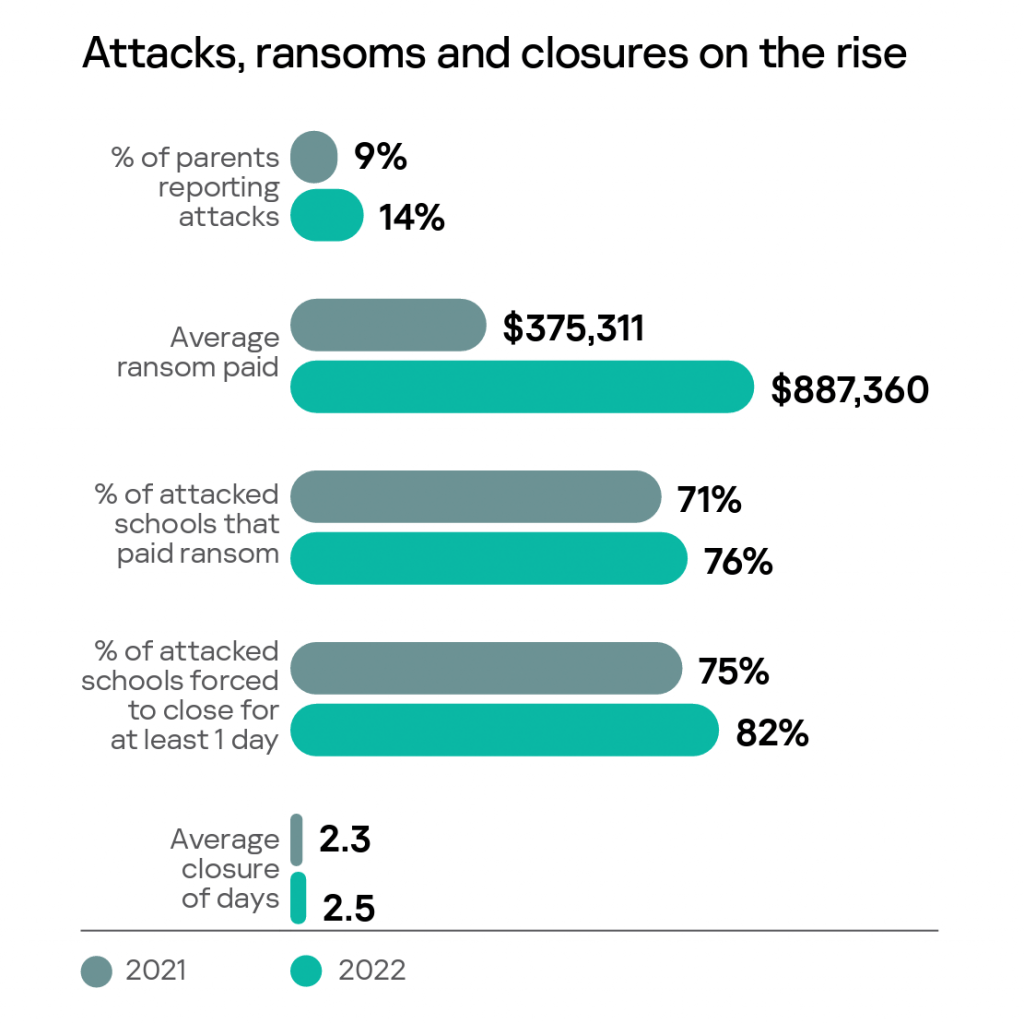
Today, ransomware is the most common way school staff experience data breaches. Phishing is a close second. But unencrypted data does find its way out of trusted hands into identity thieves.
I remember my first experience with a school district data breach. In my large urban school district, one of my coordinator-level staff decided to take work home. He decided that he wanted to spend some time tweaking the data. The deadline for preparing the data approached. Since he was working on the information on his work laptop, he took the laptop home. Less than an hour after arriving home, someone stole the laptop from the trunk of his car. With it, over ten thousand students’ and teachers’ digital records were stolen.
Since the data was not encrypted, the school district had to notify each affected individual. What’s more, the district had to invest in identity theft protection. As you can see, accidental data loss or lost devices account for approximately $1.8 million dollars.
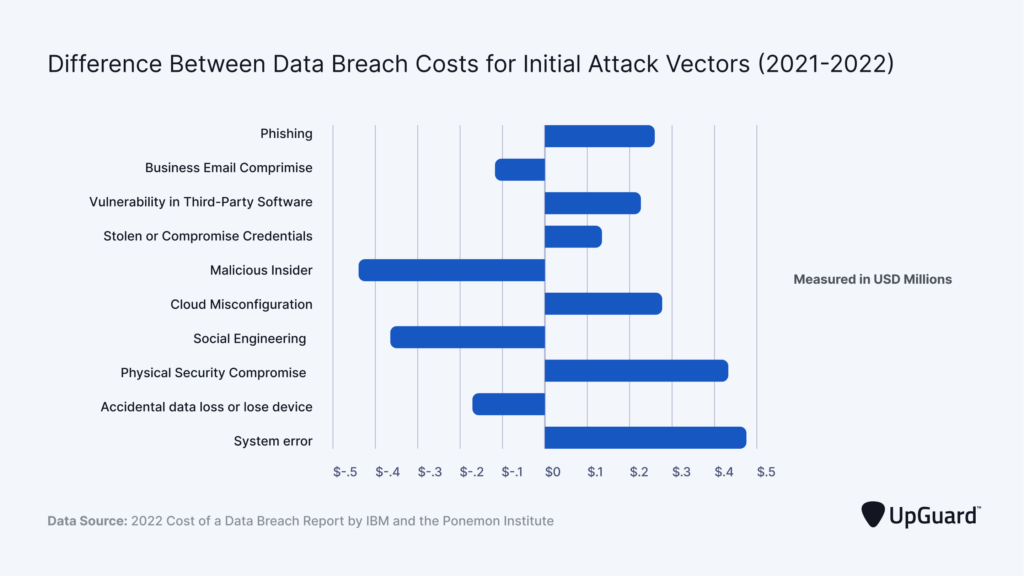
Encryption is a last-ditch effort, a protection that endures, even when other cybersecurity measures fail:
There are no perfect data security measures and security solutions. There is no way to prevent a data breach. However, even if your precautionary cybersecurity measures fail, there is a simple way to render the leaked or stolen data virtually useless to cybercriminals – data encryption.
Five Key Benefits of Data Encryption
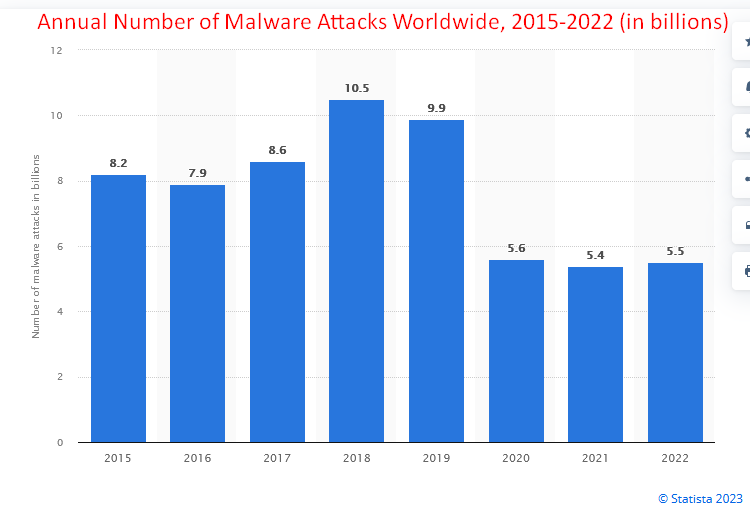
Data Breaches Happen Every Day
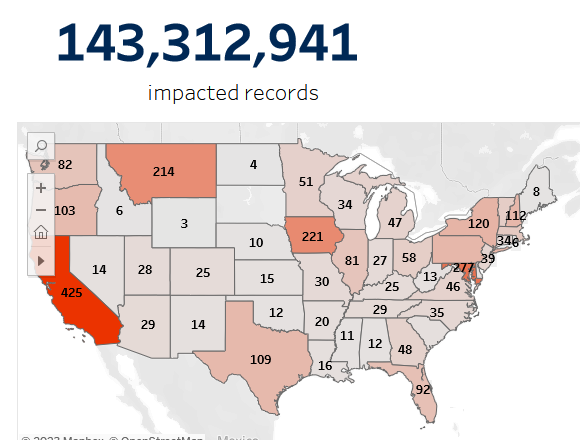
In 2022 and 2023, eight Texas school districts reported data breaches. These breaches affected 401,596 individuals. Businesses that experience a data breach should report them, and you can read up on communication expectations here:
But what about school districts? For stolen data, school districts should notify affected individuals. They should do so even if there is a cost. For example, seven of the breached districts sent letters via US Mail. Let’s estimate what the total cost would be with the total affected individuals (401,596).
- To notify each person, a letter was sent via the US Mail of the data breach. That’s an approximate cost of $76,303.24 ($.19 per item).
- Identity theft protection had to be purchased per person. The cost of identity theft protection for one year for 401,596 affected individuals is $28,633,794.
The total cost is about $29 million dollars. And that’s only eight school districts in Texas. Balance that cost with how much thieves can make for each education record (approximately $265 per student record).
How much data isn’t protected?
When responding to a survey, 96% of respondents said they carried one of the following portable storage devices:
- USB sticks
- Portable hard drives
- CDs and DVDs
According to the survey, only 28% of education professionals encrypt sensitive data. Worse, over 39% have lost a portable storage device with sensitive data. This leaves 72% of education professionals not encrypting data. That’s a problem.
How is data stolen?
Let’s look at a few real-world examples:
- A central office staff member leaves a copy of the unencrypted data on their USB drive. They take it home with them. When stopping at the store on the way home, it is stolen or falls out of their bag.
- A central office PEIMS coordinator emails an Excel spreadsheet (with a password) to a school principal. Since email is a postcard, the data is intercepted and the password cracked.
- A food service worker reads her personal email on a point-of-sale computer in the cafeteria. She saves malware on her computer that sends unencrypted data to the cloud, where ransomware developers are waiting to exploit the data.
- You send a data file packed with confidential data for staff (social security numbers, health and medical information) to human resources. The data ends up on a personal device (e.g. phone, tablet, computer) that is stolen or accessed inappropriately.
- Instructional staff posts content on a website to make it more easily accessible to campus staff. A parent finds his child’s data online.
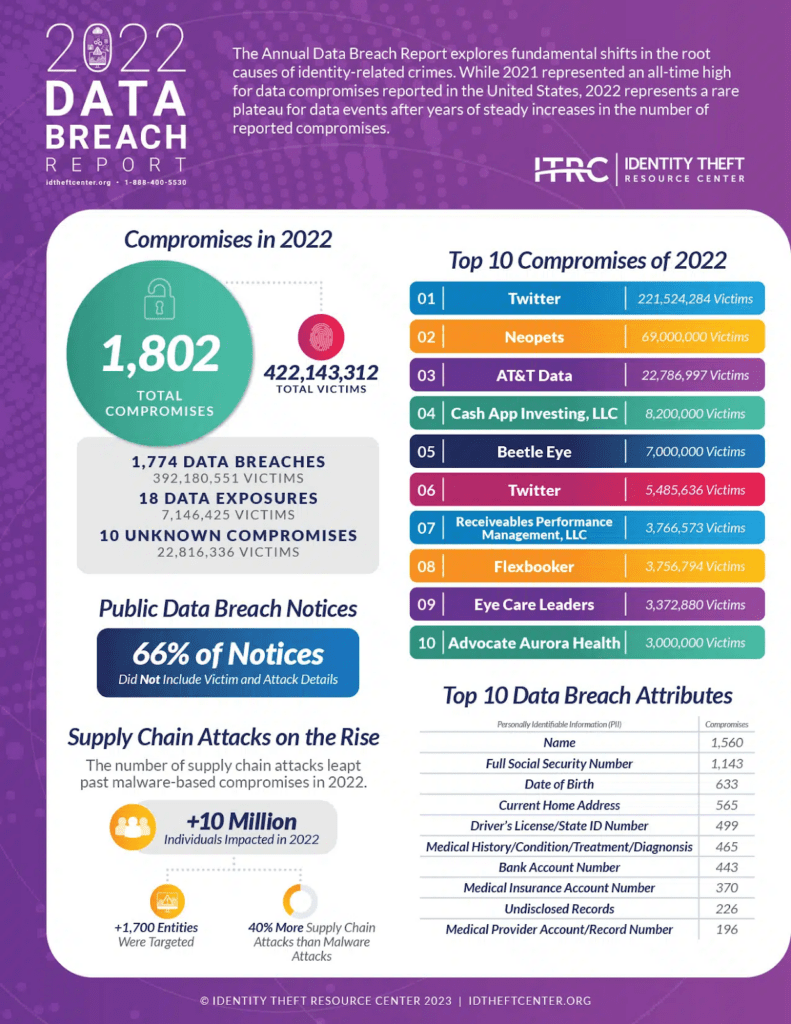
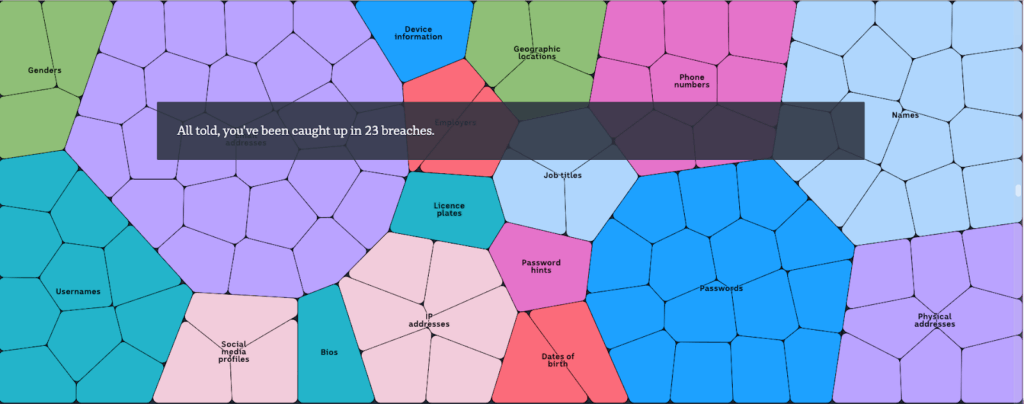
This happens more than you think. In 2022, it happened to Austin ISD, Mansfield ISD, and Judson ISD. In 2023, it happened to San Benito Consolidated ISD, Plano ISD, Lake Dallas ISD, Pearland ISD, and White Settlement ISD. In most cases, the data stolen included:
Name of individual
Address
Social Security Number Information
Driver’s License number
Government-issued ID number (e.g. passport, state ID card)
Financial Information (e.g. account number, credit or debit card number)
Medical Information
Health Insurance Information
Think of the consequences for individuals. Dealing with potential identity theft can be time-consuming and expensive. I have experienced this myself. In 2011, the Texas Teacher Retirement System (TRS) experienced a data leak. Someone at TRS placed unsecured data on a web server for download. I was one of 3.5 million affected. In a 2018 breach, affected individuals included 1.25 million Texans. These individuals counted on the Texas Employee Retirement System to keep data safe.
School district (and campus) staff have the same responsibility. The tools are free. Why not use them?
Texas Safe Habor
If a stolen USB drive has non-encrypted data, you have to take action to notify the individuals affected. However, if the data is encrypted, under the Texas Safe Harbor statute, you don’t have to say anything. Your school district does not suffer embarrassment and financial liability. Your students and staff do not have to worry about identity theft and bank fraud. That is, the school district isn’t the source of the problem.
Let’s review what “safe harbor” constitutes:
The concept of “Safe Harbor” refers to specific actions, example; encryption of private data, that an individual or an organization can take to show a good-faith effort in complying with the law. This good-faith effort provides a person or organization “Safe Harbor” against prosecution under the law (Grama, 2015, pg.253).
The State of Texas Statute 521.002 states that when an individual’s first name or first initial and last name are combined with other private information (e.g. Social Security Number), the information must be encrypted. The State of Texas Bus. & Com. Code 521.002, 521.053; Ed. Code 37.007(b)(5), and Pen. Code 33.02 all have provisions for personal private data protection, but none of these set a specific encryption standard. According to this law as long as an organization encrypts personal private information as the law specifies, theft of encrypted information would not require a breach notification which fulfills the principle of Safe Harbor (State of Texas Statutes 521.053, 2009).
Safe Harbor and the State of Texas Breach Notification Laws
The lesson is simple. Encrypt your data.
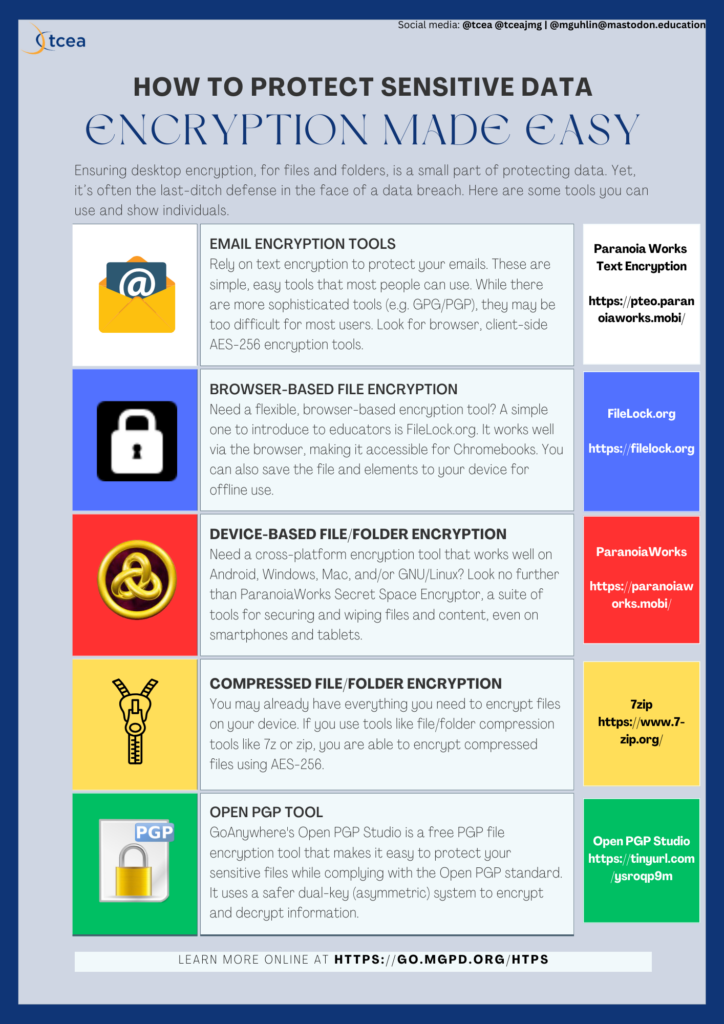
Image created by the author and shared under CC-BY-SA. Get a copy | View
Tips for Encrypting Data
Now you know you can prevent paying a single cent if you take just one action. Safeguard sensitive data with free, no-cost encryption tools. These tools rely on military-grade AES-256 encryption to protect data. Take a look at some instances when data should be encrypted:
- Encrypt all data before placing it on a USB external drive or sending it via email.
- Working with sensitive data on your device? Make sure it’s encrypted while “at rest” or not in use. Someone can steal your device, even if it is in a locked file cabinet or office.
- Going on the road? Remove confidential data from your mobile device (e.g. smartphone, iPad tablet, Chromebook)
- Working at home? Encrypt data, and/or securely delete it when finished.
Use encryption tools that offer AES-256 encryption algorithm. They are available at no cost and work on all your devices.
Advanced Encryption Standard (AES) 256 is a virtually impenetrable symmetric encryption algorithm that uses a 256-bit key to convert your plain text or data into a cipher.
Five Encryption Tools
Here are some simple tools you can use to safeguard your data for personal and/or work use. All these tools offer AES-256 encryption, work in your web browser, and are usable on Chromebooks.
- Encrypt your emails with text encryption
- ParanoiaWorks Text Encryption (Works via web browser)
- Encrypt your files or folders with file encryption tools like:
- FileLock.org (Works via web browser)
- ParanoiaWorks Secure Space Encryptor (Works on Android, Windows, Mac, GNU/Linux)
- Web Browser-Based File Encryption (Works via web browser)
- 7zip (AES-256)
Watch this short video tutorial. It features two of my favorite encryption tools: FileLock.org and Secure Space Encryptor:
In conclusion, there is significant financial and personal risk involved with not encrypting data. With the prevalence of data breaches in school districts and beyond, we must work to encrypt and protect our data to ensure a safer and more secure digital environment for students and staff. Which tools will you be using?