Technology department staff often ask how they can better secure confidential data, especially in these days of hackers and leaks. One approach involves improving the data processes themselves. Another is to coach other staff before they choose a new instructional platform. Start with Georgetown ISD’s template to get the conversation started. For technology departments, reflect on your responses to these four questions.
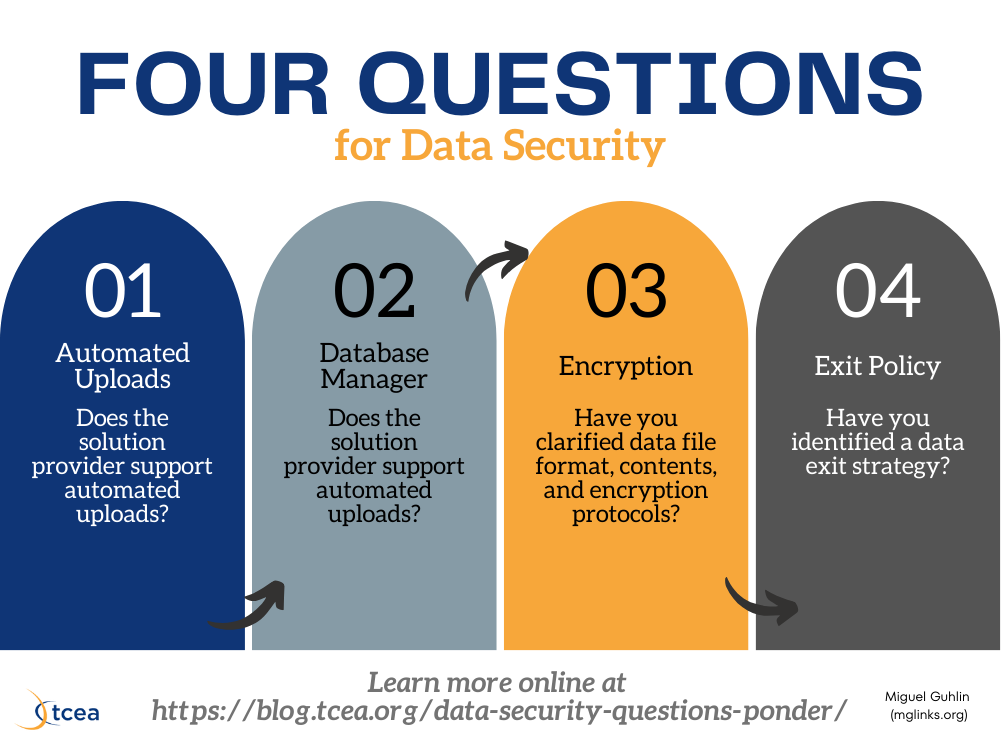
1) Does the solution provider support automated uploads?
“The classroom teacher can create the student roster, right?” says the math curriculum director. Classroom teachers should not be expected to create login credentials for each student they serve. High mobility rates make data consistency difficult. Without the ability to submit required information (via Active Directory sync or comma-delimited CSV files), schools will find themselves in a GIGO scenario (e.g. garbage in, garbage out) when updating rapidly changing data.
2) Do you have an information sherpa?
Your school district may have a standard single sign-on solution (SSO) provider, such as ClassLink, Clever, Enboard, or Identity Automation. However, a database manager will need to create the files those solutions require, including necessary login credentials. How multiple data sets intersect via courses and classes remains critical. You need a data sherpa who has the right set of skills to put the data in the correct file formats.
3) Have you clarified data file format, contents, and encryption protocols?
Some school districts lack trained staff to make the files. When that is the case, districts often turn to the SIS (Student Information System) provider. Some tips on this include:
- Communicating the name of the project contact;
- The frequency of the data refresh (i.e. both data files are to be placed on the district secure FTP server nightly;
- Encryption protocols for transfer via secure file transfer protocol and file encryption such as PGP/GPG;
- A clear delineation of data elements (e.g. student ID, first name, last name, location);
- A brief description;
- Sample data;
- Desired filename format (students.csv); and
- A text delimiter (comma, tab, or pipe). View sample form.
4) Have you identified a data exit strategy?
New projects may start with superintendent support, but then end in obscurity. At that point, the district requires an exit strategy. Before beginning work with a solution provider, both parties should sign a memo of understanding. This memo articulates the bounds of the partnership and how secure information will be stored. A data breach policy (get ebook) must also be formulated. Here is a sample memo of understanding.
Conclusion
Ensuring these questions are addressed eliminates a host of issues that result when working to setup a secure environment. So do yourself a favor and develop the answers before you embark on a new project.
