Ransomware attacks penetrated the defenses of 500 schools in 2019. The K-12 Cybersecurity Resource Center attributed only eleven incidents in 2018 to ransomware. When you think about schools, do you imagine an impenetrable fortress? Sixty-eight percent of IT leaders list cyber threats as a top priority. In spite of that, cybersecurity defenses are thin. A new report from Absolute Software describes just how thin. In July and August of 2019, the number of total security incidents jumped to 160. This exceeded the total number of incidents identified in 2018. Here are some key findings from this report released in October 2019.
While the focus on technology delivers many benefits to students and educators, it also creates more complexity — and more work for resource-constrained teams. Within a few years, K-12 IT leaders have gone from managing a couple of operating systems, a handful of apps, and a few hundred devices to managing hundreds of versions of operating systems, apps, and extensions; and thousands of devices.
Finding #1: K-12 Schools Are Digital Now
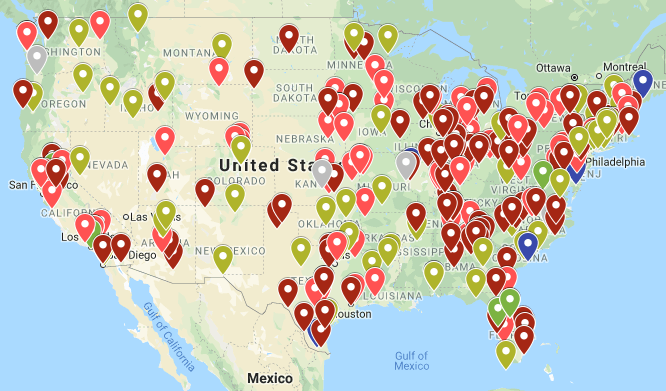
In compiling data for their report, Absolute Software discovered some startling information. For example, ninety-four percent of schools have high-speed internet. In schools, technology spending has increased sixty-two percent from 2016 to 2019. And eighty-two percent of districts provide student devices in one-to-one or similar programs. But going digital has consequences for schools, exposing them to fresh dangers. For example, since 2016, there have been 700+ cybersecurity incidents. Schools are the second highest target of ransomware. See the interactive map below. Olive green bubbles represent education.
Did You Know?
To combat ransomware, the U.S. Senate and House have passed legislative bills to create the DHS Cyber Hunt and Incident Response Teams Act. DHS will “maintain cyber hunt and incident response teams to help private and public entities (like schools, students, employees, local government) defend against cyber-attacks.”
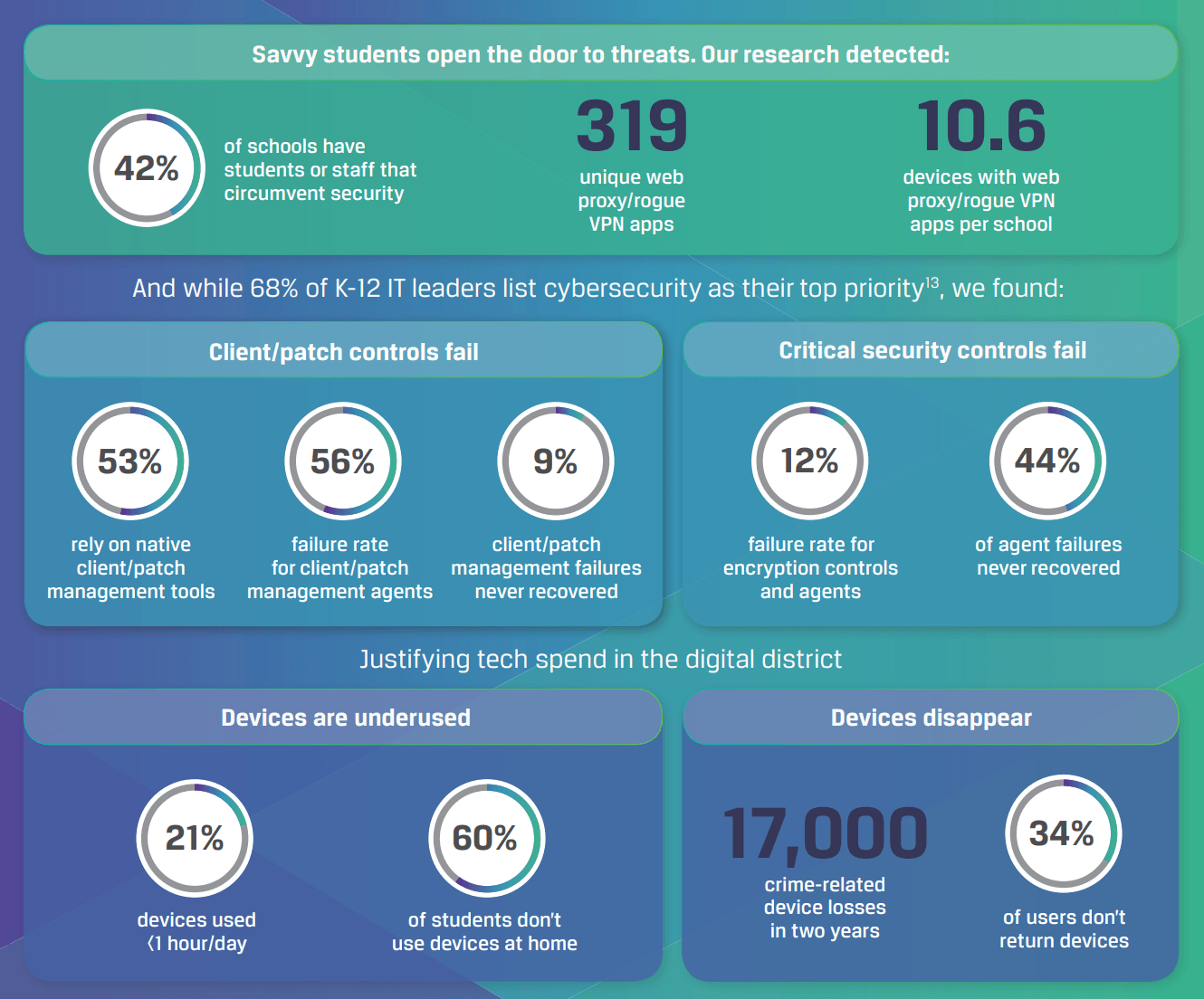
In spite of schools going digital, twenty-one percent of devices are used less than an hour a day. Approximately 60 percent of students don’t use devices at home. Putting devices in schools has resulted in 17,000 crime-related device losses in two years. Of those who use school devices, thirty-four percent fail to return them.
Students themselves are doing everything in their power to circumvent those protections. There may be no malicious intent — the students just want access to content that may be restricted on school devices — but their actions create gateways for malicious outsiders.
Finding #2: Staff and Students Open the Door
“Educators in all contexts need to open the door to authentic teaching and learning,” says Wes Fryer. Unfortunately, a lot has changed since 2006 when Wes said that. Forty-two percent of schools have students or staff that actively circumvent security. This often comes in the form of unique proxies or rogue virtual private network (VPN) apps. When schools opened the door, more than authentic teaching and learning snuck in.
With an average of 10.6 devices per school harboring web proxies and rogue VPN apps, schools are also at risk of non-compliance with applicable student safety laws.
Finding #3: Digital Tech, A Management Challenge
Spending time troubleshooting a device in class wastes instructional time. When devices fail, schools rely on native client/patch management tools. With so many different devices and operating systems in schools though, there is no one tool for all. For example, consider that Absolute Software found the following was true:
- 93 percent of schools manage up to five versions of common apps
- 137,000 unique application versions
- 6,409 unique Chrome OS extensions
- 11 device types
- 258 unique operating system versions across Windows, Chrome, Mac, and others
Managing that many different systems and devices could give anyone a headache. It’s no wonder technology departments like to standardize on platforms and tools. To manage them, they bring in various client management systems. Of those, there is a fifty-six percent failure rate of client management tools. To close the gap and make things work, technicians have to engage in a manual resolution process. Worse, most departments are under-staffed. This means you have a perfect storm for data breaches.
Our study reveals that schools that have encryption in place experience agent failures on an average of nine devices per day — almost half of which never recover, leaving students and staff at risk of potential data breaches
Finding #4: Underutilized Devices
One of the most disheartening points in this report speaks to underutilized devices. Whether on or off campus, many devices are used for less than an hour a day. Twenty-one percent of devices fall into this category. Sixty percent of students don’t use devices schools have purchased for them at home.
In my own experience, this can mean that devices that sit idle are easy targets for theft. Thirty-four percent of users fail to return devices at school year’s end. That is, these devices are “lost or stolen.” Another eye-opening statistic? Forty-six percent of devices are stolen from cars. Some of those devices will contain sensitive data that is not encrypted (Learn more about Texas Safe Harbor and encryption via this Wakelet).
It is irresponsible to invest more public dollars into new security technologies if the basic measures — visibility, control, and resilience — are not operating effectively first. Getting the basics right will enable IT leaders to redirect this budget toward enhancing or expanding digital equity initiatives.
Finding #5: Solutions
The report offers potential solutions. It encourages schools to start by getting the basics right. With K-12 technology spending set to grow to $342 billion by 2025, the basics are important. Those basics include:
- Visibility: Better awareness of what happens on student-managed devices
- Control: Tighter controls over what gets put on devices
- Resilience: Ensure basic tools work and use funding to get tools that fill the gaps
End-user training (e.g. staff, students) remains an ever-present high priority.
Critical Questions to Ask
How is your technology department strengthening the basics? How are you addressing the need for end-user training in a comprehensive way? How are you ensuring technical staff have the support and training they need? Yesterday, you could hire low-paid high school graduates. Today, they need a world-class education in cybersecurity and client management. How are you closing the gap?
Schools have gone digital, and with digital learning comes a host of problems. Chief among them are increasing ransomware attacks, difficult device management, and data breaches. To resolve these issues, schools need to get the basics down and close the gap in end-user training.


1 comment
I would think that the age of the devices would also be a consideration when trying to avoid attacks. Good information and lots to think about.