If you have missed the recent news about two computer chip-based vulnerabilities, count yourself fortunate. These vulnerabilities affect every device sporting an Intel chip, which has serious implications for schools. The Meltdown and Spectre vulnerabilities can open the door to hackers who can get apps or software onto your device of choice. That’s not as hard as you might think. Worse, computer chip maker Intel says they are releasing updates for all devices made in the last five years. Yes, that’s right, fellow technology directors. It’s time to discard those old five plus year old CPUs and upgrade. What a golden opportunity for comprehensive equipment replacement.
Affected Devices
Affected devices include probably every piece of technology, except maybe Raspberry Pi, you have in your schools or at home:
- Desktop and laptop computers (Mac, Windows, GNU/Linux)
- Servers featuring Mac, Windows, GNU/Linux operating systems, including virtual machines
- Chromebooks
- Apple iPhones and iPads
- Android smartphones and tablets.
Meltdown and Spectre
“The two hardware bugs can be exploited to allow the memory content of a computer to be leaked. Such a leak could potentially expose stored passwords and other sensitive data, including personal photos, emails, and instant messages,” says Alastair Jamieson, NBC News. Wondering what might happen? Watch this short video to get insight into the problem.
These two malware processes can skim private or confidential data from your device, including encryption keys your device uses. This is a hardware design problem rather than a software problem. The easiest way to solve the problem per US Cert’s Vulnerability report, as cited in this video when the problem first arose, is to replace your device (Source). Yikes! For some districts, that’s the long-term fix.
In the short term, you have to mitigate the vulnerabilities. To do that, be sure to update your device’s operating system, as well as follow the steps suggested below.
Taking Action
Want to take action, but not sure what to do? Here are some next steps to take now organized by device. I’ve read numerous reports and condensed what you need to know in the space below.
Google has provided a detailed response to the vulnerabilities. Let’s take a quick look at some affected aspects of Google devices and services.
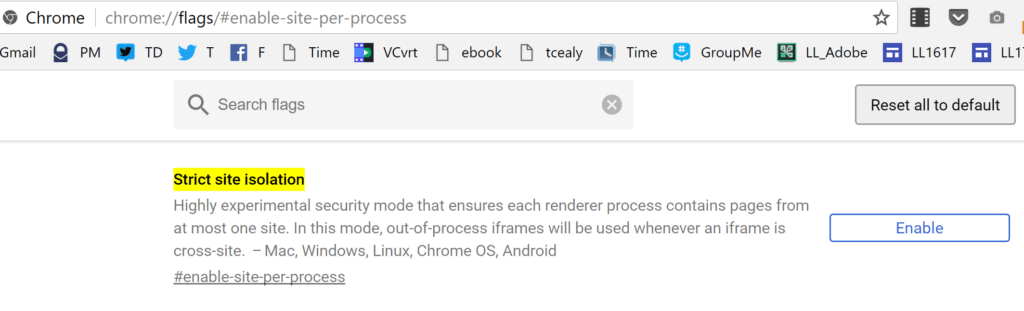
For the Chrome browser, you can enable an optional feature in the Chrome browser. The feature is known as “Site Isolation.” Enabling this feature mitigates the vulnerabilities. The feature, once enabled, isolates websites into separate address spaces. The benefit? It prevents an attacking website you have visited from obtaining your login and password credentials for another (Source).
Here’s how you can keep your online login/password from being stolen:
1) Copy-and-paste the following into your Chrome browser:
chrome://flags/#enable-site-per-process
2) Then, click ENABLE, as shown below:
Here are some other affected devices. You can see the complete list online at Google’s site:
- Chromebook: For your Chromebook, updates are already rolled out or in process. Google’s website shares “OS versions prior to 63 are not patched. Chrome OS systems started receiving version 63 on 2017-12-15. Some Chrome OS devices are end of life and no longer receiving updates. To check your specific model, see this page.” For example, I can check on my Acer C720 Chromebook online to see if “mitigations” are available yet. The Acer C720, unfortunately, shows “No.”
- Android: For your Android device, it will be difficult for these vulnerabilities to be exploited. Future updates for Android devices will address the vulnerability.
The following are NOT affected: Google Suites/GoogleApps, Google Home/Chromecast, and Google Hub/WiFi.
Microsoft
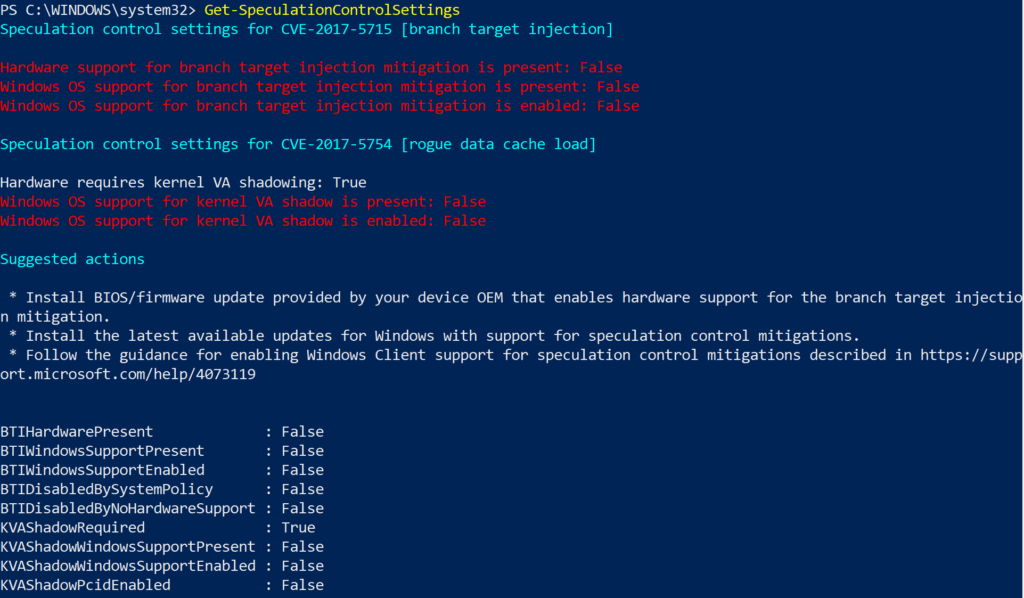
Microsoft has recommended that Windows 10 updates be completed prior to adding firmware updates. You will want to:
- Make sure that you have compatible antivirus programs installed (e.g. BitDefender Free is one of my favorites, but not yet on the approved list via Security Researcher Kevin Beaumont’s list as cited here and here).
- Apply all available Windows operating system updates, including January, 2018 Windows security updates.
- Apply the firmware update for your particular device.
As you can see from the screenshot above, my own Microsoft Surfacebook running Windows 10 features “False” as the setting for most items. Unfortunately, those should all be set to “True.” To go through this process, you will need to follow the process outlined at Microsoft’s website.
Apple
Meltdown and Spectre also impact Apple users. That’s right, if you use a Mac or iOS device (e.g. iPhone, iPad), you are affected. Here’s what you can do to protect your iOS or Mac device:
- Install all updates on your iOS device as soon as they become available. iOS users should already have access to an update to their Safari browser (which may mean you use that browser exclusively…hmm).
- Only install new apps from the approved Apple store (which means jail-broken iPhone users will want to be extra careful. Thank goodness, those are rare in K-12 school settings, except for high school BYOD situations).
How Do I Begin?
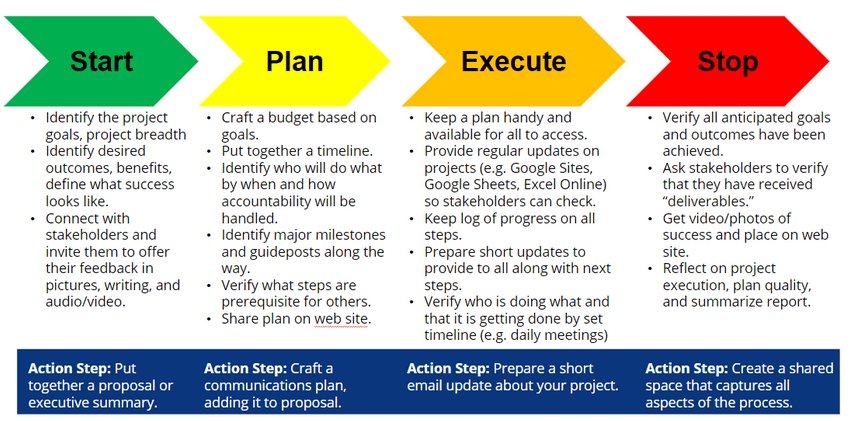
If you’re a technology director, you need to take a few steps to prepare for the coming hardware meltdown. If you don’t already have an equipment replacement plan in place with a secured budget, then you need to get one in place. Want to learn how to engage in project management (and, wow, you are going to need it), then why not sign up for TCEA’s Project Management Fundamentals webinar? Be sure to follow the project management action steps I adapted for K-12 education and have used successfully: