Every other week, I read or hear about a school district that has suffered a phishing attack, an approach distributed by email designed to trick you into giving your email username and password to criminals. Dealing with ransomware (a form of software that infects your machine when you double-click on it and encrypts your files, then demands you pay them for decrypting them) can be embarrassing, since it may result in the district having to pay to get its data. Or you could lose the data and tell only the federal auditors coming to evaluate your records for the last five years.
In addition, ransomware may also be distributed to district users via email. Several districts and Texas education service centers have allegedly faced some of these challenges (allegedly because ransomware infestations travel through word of mouth):
It’s…thrown a kink in the school district’s scheduled…exams…The crypto-ransomware “has affected the district’s entire operations from internal and external communications to its point-of-sale for school lunches. It also has prevented any students from taking the scheduled…exams, which are entirely computerized.” Source: Network World
- Look before you click. Avoid clicking on email attachments that come from people you do not know. Email attachments with “exe” and “zip” are suspicious. Also, do NOT go into your SPAM folder and click on the email attachments.
- Connect before opening. Ask yourself, “Was I expecting a file from this person?” If yes, connect with them via phone, social media, or email and ask, “Did you send me this file?” If the answer is “no,” then delete it.
- Avoid clicking on email attachments via your personal email on a work computer, especially if it’s a Yahoo email account. Multiple types of malware spread ads via that one service alone.
- Scan files before opening them. You can right-click a file, save it to your computer, and then choose to virus scan it before opening it.
- Backup your data to a cloud drive storage provider (e.g. OneDrive, Google Drive, Dropbox). Ransomware can spread via cloud storage where your files are automatically backed up when you place them in a certain folder (e.g. Dropbox), so be aware that ransomware WILL encrypt those files and the encrypted files will be backed up. Back up manually to the cloud and/or to external USB drives. Avoid leaving the latter connected to your computer.
Staff that succumb to phishing attacks open the organization’s virtual doors to a ransomware infestation. For example, in my inbox, I received an email purporting to be from a colleague sharing some files with me via Dropbox, but this looked like a phishing attack. Let’s go through the process I went through together. 
Knowing that my colleague did not send this email, I opened up a fresh browser where I’m not logged into anything and tried the link: It didn’t work. That’s good! But if it had been a phishing scam, something like this would have popped up: When you examine the “Click here to view” link, you will find as I did that the link is to a non-Dropbox web site in the UK. That suggested to me that this link did NOT originate with Dropbox. As a result, I contacted my colleague via Twitter and asked, “Did you send me something via email that originated on Dropbox?” He responded after a short delay, “No, I didn’t.”
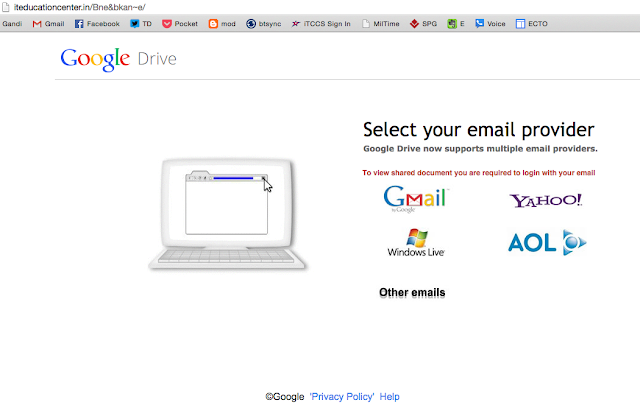
Notice how the screen to the left offers you the opportunity to compromise your login and password for multiple email providers. This suggests that the goal is to steal ANY email account credentials you have. This can be potentially catastrophic since school district personnel often save student/staff confidential content in the cloud.
Actual Example: One principal was shocked when her Google Apps for Education account started sending out phishing attacks to all the email lists she was a member of, including the district-wide principals’ list, her campus staff list, and district-wide news list. And her shock turned into horror as colleagues clicked and were infected themselves. Horror shifted to shame as her colleagues grew angry, inquiring why she had inflicted them with this plague of phishing. And all the principal had done was fall prey to a phishing attack from a dear friend.
I have all of the following on my personal Windows computer and wouldn’t dream of using it without having them installed. In spite of the fact that Windows Defender comes standard on Windows 10 computers, it’s important to have anti-malware and antivirus software loaded and working.
- List of Mac AntiVirus Solutions
- Windows Solutions:
- Anti-Malware
- Malware Bytes* – Great to use when you think your computer has been infected with malware/spyware and you need your computer “cleaned out.”
- AntiRansomware – Although still in beta, Malware Bytes’ solution to ransomware offers real-time protection against ransomware, catching it before it can encrypt your files.
- Spyware Blaster*– An easy to use “inoculation” program against spyware/malware.
- Spybot Search and Destroy* – The best part of Spybot is the TeaTimer which protects your computer’s registry against contamination and immunizes your browsers (IE, Firefox) against malware.
- AntiVirus
- BitDefender Free – This free for home use antivirus works great and does not drive you crazy with advertisements.
- Sophos Home Antivirus – This is another protection free for home use.
- Anti-Malware