Are you a school district technology leader? If you are, you have a tough responsibility. That duty is protecting student data privacy. And, at the same time, you must balance new, popular, and innovative educational technologies. How can you ensure student privacy and review new solutions pushing their way into the classroom are safe? TCEA’s PROTECT rubric (view | get a copy) offers a practical framework for evaluating and implementing privacy-conscious tools. You also can try it out via custom GPT.
Three Key Points for K-12 Technology Leaders
1. Prioritize Parental Rights and Transparency
“The most important thing is to make sure that technology is not just available but that it’s being used effectively to support learning.” – Karen Cator, Former Director of the Office of Educational Technology at the U.S. Department of Education
Are your ed tech solutions clear about parental rights and data usage? If not, you may need to check in with your vendor or solution provider.
2. Implement Robust Data Retention and Deletion Policies
“Cybersecurity is a shared responsibility that requires ongoing collaboration between school staff, students, and families.” – Amy McLaughlin, Cybersecurity Project Director.
One question to consider is, “What is the Ed Tech vendor’s student data retention policy?” An important follow up is, “What happens to that data when the relationship is over? How does it get deleted, and how do you get a secure copy of it?” Not getting straight answers or setting up arrangements at the start of the relationship can potentially result in a rocky, embarrassing ending.
3. Enhance Security Measures
“Security is always going to be a cat and mouse game because there’ll be people out there that are hunting for the zero day award, you have people that don’t have configuration management, don’t have vulnerability management, don’t have patch management.” – Kevin Mitnick, Cybersecurity Consultant and Former Hacker
The question to consider here is, “Are your ed tech solutions employing state-of-the-art security practices?” Two nonnegotiable practices are multi-factor authentication and end-to-end encryption.
Introducing the TCEA PROTECT Rubric
Now, let’s take a look at a process you can put in place: TCEA PROTECT.
The PROTECT rubric addresses key aspects of student data privacy, including:
- Compliance with major regulations like FERPA, COPPA, and GDPR.
- Data collection, use, and sharing practices.
- Security measures and encryption.
- Parental rights and access to student data.
- Age-appropriate considerations for under-13 and under-18 users.
- Transparency in data practices and third-party relationships.
- User control over data, including deletion and opt-out options.
With PROTECT, educators, administrators, and parents can quickly assess whether an educational technology solution meets the necessary standards for protecting student data privacy across different regulatory environments.
Note: Directions for using the PROTECT rubric with an AI tool appear at the end of this blog entry.
Now that you are aware of key aspects, let’s dig a little deeper into each aspect.
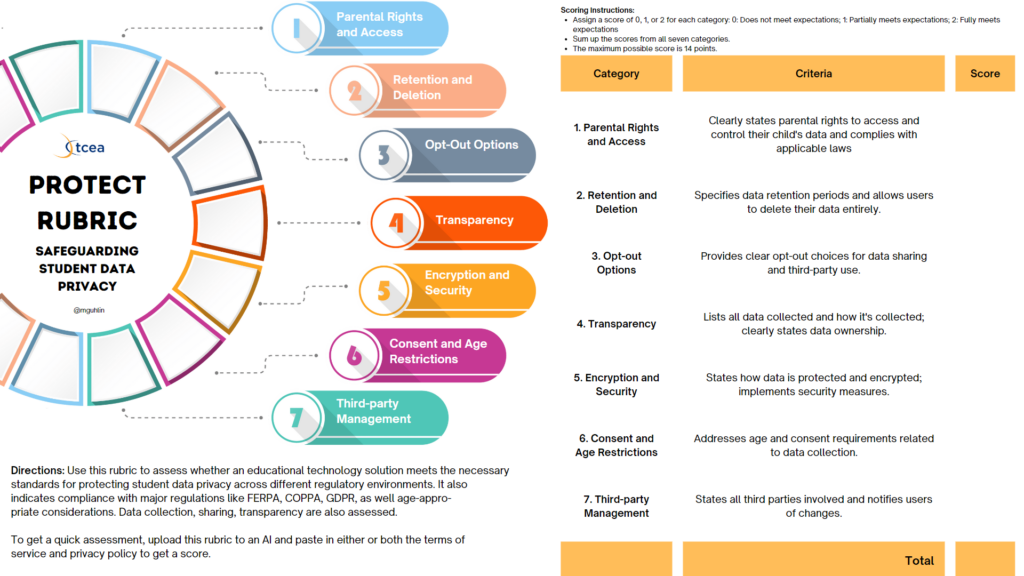
PROTECT Rubric Components
The rubric has several components, matching the letters of the PROTECT acronym. Let’s review each in turn below.
P – Parental Rights and Access
- Clearly states parental rights to access and control their child’s data
- Complies with FERPA (USA) and GDPR (EU) requirements for parental access
R – Retention and Deletion
- Specifies data retention periods
- Allows users to delete their data entirely
- Complies with data minimization principles
O – Opt-out Options
- Provides clear opt-out choices for data sharing and third-party use
- Allows users to opt-out of targeted advertising
T – Transparency
- Lists all data collected and how it’s collected
- Clearly states data ownership
- Discloses all third-party data sharing
E – Encryption and Security
- States how data is protected and encrypted
- Enforces strong password creation
- Implements multi-factor authentication
C – Consent and Age Restrictions
- Addresses COPPA (USA) and GDPR (EU) requirements for under-13 users
- Clearly outlines consent mechanisms for data collection and use
T – Third-party Management
- States all third parties involved and information shared with each
- Requires third parties to adhere to the same privacy standards
- Notifies users of changes in third-party relationships
Now, let’s turn our attention to the implementation of the PROTECT process in your organization.
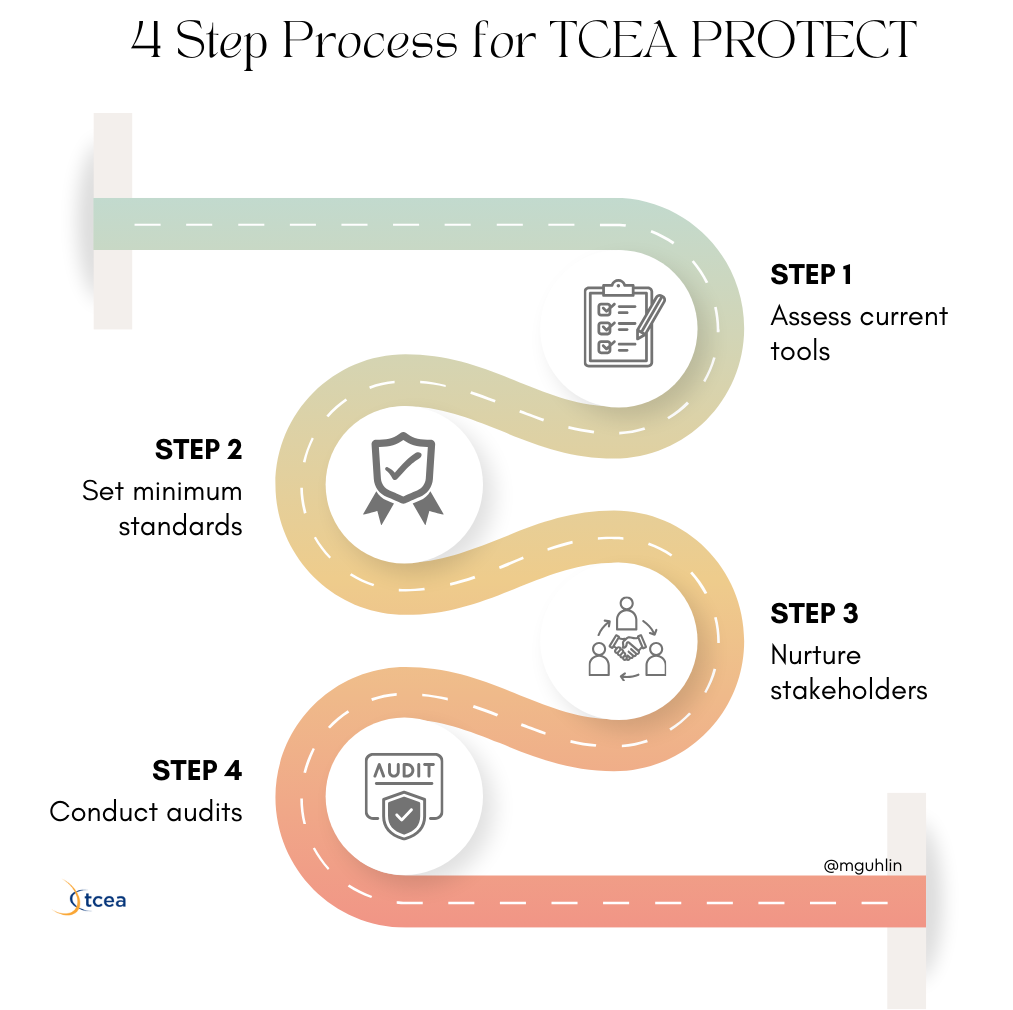
Implement the TCEA PROTECT Process
The TCEA PROTECT rubric provides you with a tool that you can use to effectively assess your current solutions. Rely on it and your favorite AI solution to do the following:
- Assess Current Tools: Apply the rubric to existing technology solutions to identify areas for improvement.
- Set Minimum Standards: Decide what is a minimum acceptable score for new digital tools and services.
- Nurture Stakeholders: Provide professional learning to your teachers, administrators, and IT staff on using the rubric. They can easily use it to assess potential purchases.
- Conduct Audits: Perform annual privacy audits using the rubric. This can help with locking in compliance and modeling best practices.
How To Get Started
Want to facilitate professional learning in your school district around TCEA PROTECT? Consider providing learning opportunities through these activities below.
| Activity | Description | Participants |
|---|---|---|
| Privacy Audit Workshop | Train staff to use the PROTECT rubric for evaluating edtech tools | IT Staff, Curriculum Leaders |
| Vendor Communication Session | Practice clear communication with vendors about privacy expectations | Technology Directors, Procurement Team |
| Parent Privacy Night | Educate parents on district privacy practices and their rights | Parents, School Leaders, IT Staff |
| Student Data Rights Lesson | Develop a lesson plan for teaching students about their data rights | Teachers, Curriculum Developers |
How To Use TCEA PROTECT With AI Support
Ready to give PROTECT rubric a spin? Some points to keep in mind:
- The maximum score possible is 14 points. A higher score indicates better alignment with student data privacy best practices and regulations.
- Use an internet-connected AI solution, such as MS CoPilot, ChatGPT Plus, You.com, or Perplexity.
- Assess a few digital tools using different AI tools to see how each AI applies the rubric, and review the scores yourself.
- Use the rubric to assess the Privacy Policy and/or Terms of Service for an Ed Tech solution.
Here are some popular AI tools scored with PROTECT. Since scores can vary between AI chatbots, and rubrics can be inaccurate (which is why you may not use them for student assessment), I’ve grouped scores by AI chatbot. I’ll share trends on scoring for each chatbot afterwards.
Scorer: Claude.ai (Pro version)
- Curipod (TOS / Privacy) scored 12 out of 14. View complete results.
- Goblin Tools (TOS / Privacy) scored 5 out of 14. View complete results. (The About page was substituted for TOS, no doubt accounting for low score).
- MagicSchool.ai (TOS / Privacy) scored 12.8 out of 14. View complete results.
Scorer: Perplexity.ai (Pro version)
- Curipod (TOS / Privacy) scored 11.6 out of 14. View complete results.
- Goblin Tools (TOS / Privacy) scored 4.4 out of 14. View complete results.
- MagicSchool.ai (TOS / Privacy) scored 11.2 out of 14. View complete results.
Let’s take a closer look at the AI analysis of these three solutions.
Using AI and TCEA PROTECT To Analyze
As you can see, the scores are quite similar, with the largest discrepancy being for MagicSchool.ai. Claude.ai gave higher scores. It also allowed for multiple documents to be assessed within a single Project, while keeping each separate for easy citation, facilitating comparison and sharing. In analyzing Goblin Tools, it’s clear that it lacks the complexity of the other two tools (e.g. Curipod and MagicSchool). But that does not excuse it from beefing up its TOS and Privacy policy to cover the bases delineated in the PROTECT rubric. Specific feedback for each vendor can be found in the complete results.
| AI Tool | Claude.ai Score | Perplexity.ai Score |
|---|---|---|
| Curipod | 12.0 / 14 | 11.6 / 14 |
| Goblin Tools | 5.0 / 14 | 4.4 / 14 |
| MagicSchool | 12.8 / 14 | 11.2 / 14 |
In spite of my concerns about the AI use of rubrics to score documents, these results from two different AIs are consistent with one another. Both Claude.ai and Perplexity.ai appear to be capable of assessing AI tools’ Terms of Service and Privacy policies using the PROTECT assessment prompt. The choice between them may depend on your access to the tool, and your preferences for the interface and workflow.
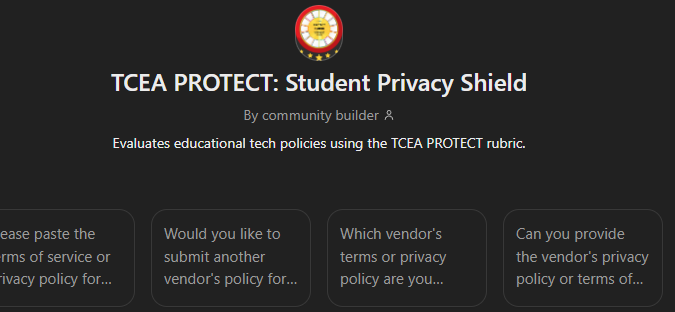
TCEA PROTECT: Student Privacy Shield Tool
Ready to evaluate privacy policies and terms of service for your favorite Ed Tech solutions? While you can use the rubric’s instructions with any AI, a ChatGPT custom GPT has been set up you can use. Access it online.
Conclusion
The PROTECT rubric provides a structured approach for K-12 technology leaders to assess and improve student data privacy practices. It does so by focusing on parental rights, data retention, and security measures. This makes it easier to create a safer digital learning environment.
The TCEA PROTECT rubric can help you as a K-12 technology leader to safeguard student data privacy as you implement innovative solutions. Establish the TCEA PROTECT process in your school district today. If you need assistance, please reach out to Director of Professional Development, Miguel Guhlin at mguhlin@tcea.org.
Additional Resources
- Student Data Privacy Consortium: Privacy resources and tools (K-12)
- Protecting Privacy in Connected Learning: Toolkit for school system leaders (K-12)
- Future of Privacy Forum: K-12 privacy research and guidance (K-12)
Related TCEA Blog Entries
- Cybersecurity Best Practices for Schools: Essential security measures for K-12 institutions
- Digital Citizenship in the Classroom: Teaching students responsible online behavior


2 comments
Bravo Miguel!
Your insight is inspiring. I’m quite a bit behind the AI trend, but obviously like you I have had questions about the potential risks to our clientele. With this tool in hand, navigating the AI headwaters becomes a manageable task.
Thank you!!
Jim, thanks so much for your kind remarks. We are all learning together, aren’t we? I’d love to know how you are using/modeling AI for your team at Shepherd of the Hills Lutheran school. You might also explore the TCEAIgnite website at https://tinyurl.com/tceaignite for additional tools and resources.
Do let me know if you’d like to have an on-site consultation for professional learning opportunities for school leaders and educator team.
Warm regards,
Miguel Guhlin
mguhlin@tcea.org